In Laravel web application development, security is one of the essential paramount. As the digital landscape continues to expand, the Importance of security in web applications, particularly those built on the Laravel framework, has reached an all-time high. In this era of interconnectedness, where information flows seamlessly across the virtual realm, the potential threats and vulnerabilities have also escalated.
The landscape of online threats has grown more sophisticated, encompassing various malicious activities ranging from data breaches to identity theft. This evolving threat landscape calls for a steadfast commitment to proactive security measures. Waiting for a security breach before addressing vulnerabilities is a risk no modern developer can afford to take.
The significance of bolstering security in Laravel web application development. While Laravel provides a robust and versatile platform for creating dynamic web applications, it’s essential to recognize that even the most advanced framework is not immune to potential security breaches. As your Laravel application evolves, it becomes a showcase of your technological prowess and a potential target for cyber threats.
The Importance of proactive security measures should be highlighted further. Developers and businesses must adopt a security-first mindset when crafting their digital creations, which means staying informed about the latest security trends, continuously updating and patching the application, and adhering to best practices for safeguarding sensitive user data.
We’ll delve into 10 critical checkpoints that can significantly enhance the security of your Laravel web application. These checkpoints encompass a comprehensive approach to securing various aspects of your application, from authentication and authorization to protecting against common web vulnerabilities. By diligently implementing these checkpoints, you’ll be taking a substantial stride towards fortifying your Laravel web application against the ever-persistent threats lurking in the digital domain.
Related Article: Laravel Web App Development: 11 Types of Web Apps You Can Build with Laravel
10 Key Checkpoints to Focus On
Here’s your comprehensive Laravel Security Checklist to ensure a robust and safeguarded web application.
1. Secure Authentication and Authorization
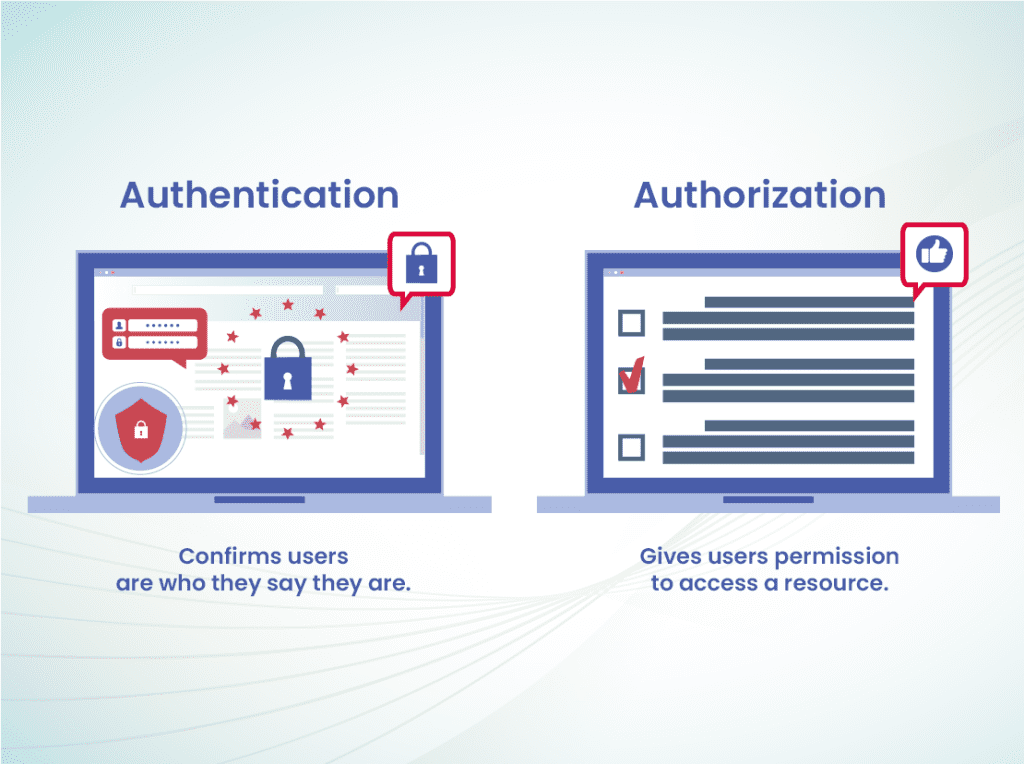
In the intricate world of Laravel web application development, security is an indispensable pillar for creating a trustworthy and resilient digital presence. One of the cornerstone elements in this security fortress is the implementation of secure authentication and authorization mechanisms. Let’s delve into how these critical aspects are pivotal in fortifying your Laravel application against potential threats.
Secure Authentication: Building the First Line of Defense
Authentication is verifying the identity of users attempting to access your application. It forms the cornerstone of security by ensuring that only authorized individuals can interact with sensitive data and functionalities. In the realm of Laravel, this process is made significantly more manageable through the framework’s built-in authentication features.
Implementing secure authentication involves:
- Strong Password Policies: Enforce complex passwords, combining uppercase and lowercase letters, numbers, and special characters. Laravel provides password validation rules to help you accomplish this.
- Two-Factor Authentication (2FA): Enhance security by requiring users to provide an additional authentication factor beyond their password. Laravel offers seamless integration with 2FA for an added layer of protection.
- Account Lockouts: Implement mechanisms that lock accounts after a specified number of unsuccessful login attempts, preventing brute-force attacks by temporarily halting further login attempts.
Authorization: Ensuring Granular Access Control
Authorization, however, deals with controlling what authenticated users can do within the application. It’s about granting permissions and access rights based on roles and responsibilities, ensuring that sensitive actions are restricted to those who need them.
Key steps in implementing effective authorization include:
- Role-Based Access Control (RBAC): Define roles such as “admin,” “user,” or “manager,” and associate them with specific permissions. Laravel’s RBAC system lets you assign roles and permissions effortlessly.
- Middleware Authorization: Leverage Laravel’s middleware to restrict access to routes or controllers based on user roles or custom conditions. This is a powerful way to ensure that only authorized users can perform specific actions.
- Resource Controllers: Utilize resource controllers to create a consistent and structured approach to handling CRUD operations. These controllers can be easily configured to enforce authorization rules for specific actions.
- Dynamic Authorization Policies: Laravel’s policy system lets you define authorization logic in a structured manner. It’s beneficial for complex access control requirements and allows for fine-grained control over what users can do.
In a world where digital threats are evolving rapidly, securing your Laravel application’s authentication and authorization processes is paramount. By implementing robust authentication mechanisms and enforcing precise authorization rules, you’re safeguarding sensitive data and building a foundation of trust with your users. Remember, security isn’t just a one-time task; it’s an ongoing commitment that requires vigilance and adaptability in the face of ever-changing cyber threats.
2. Keep Laravel and Dependencies Updated
In the dynamic realm of Laravel web application development, staying ahead in the security game is an ongoing endeavor. One of the fundamental practices that forms the bedrock of a secure digital presence is the consistent updating of your Laravel framework and its associated dependencies. Let’s explore why this practice is essential and how it contributes to the overall security of your application.
The Power of Regular Updates
Technology, much like the world around us, is in a constant state of evolution. This evolution is driven not only by innovation but also by identifying and rectifying vulnerabilities and weaknesses. In the context of Laravel development, regular updates to both the core framework and its dependencies play a pivotal role in ensuring the security and stability of your application.
Why Updates Matter:
- Security Patches: Vulnerabilities can emerge at any software lifecycle stage. Developers and the open-source community work diligently to identify and address these vulnerabilities. Regular updates ensure that your Laravel application is fortified with the latest security patches, minimizing the risk of exploitation.
- Compatibility: As Laravel evolves, updates often improve compatibility with newer PHP versions, web servers, and databases. Staying updated ensures your application remains in sync with the broader web development ecosystem.
- Performance and Features: Updates not only fix issues; they also introduce performance enhancements and new features. Embracing these updates can lead to a more efficient application that delivers a better user experience.
Dependencies: Handle with Care
Laravel development heavily relies on various external packages and libraries. While these dependencies contribute to the efficiency and functionality of your application, they can also introduce vulnerabilities if not managed appropriately.
Best Practices for Dependency Management:
- Regular Audits: Periodically review the dependencies your Laravel development company utilizes. Check for any vulnerabilities reported in these packages and prioritize updating them accordingly.
- Automated Tools: Leverage automated tools that can scan your project’s dependencies for known security issues. This can help you identify potential risks and take corrective action swiftly.
- Version Pinning: Specify the exact versions of dependencies your application uses. This prevents unexpected updates that might introduce breaking changes or vulnerabilities.
In the rapidly evolving web application security landscape, treating updates as a proactive security measure is paramount. By ensuring your Laravel framework and dependencies are up to date, you’re demonstrating a commitment to maintaining a robust digital fortress for your application. This safeguards sensitive user data and positions your Laravel development company as a conscientious custodian of digital security. Remember, in technology, staying current isn’t just an option—it’s necessary for a secure and successful future.
3. Validate User Input
The ever-evolving landscape of Laravel development, the adage “Garbage In, Garbage Out” holds immense relevance. One of the pivotal checkpoints in ensuring the robustness of your Laravel application’s security is the validation of user input. Let’s dive into why validating user input is crucial and how it is a formidable shield against potential vulnerabilities.
The Essence of User Input Validation
User input is the gateway through which your Laravel application interacts with its users. Whether it’s a login form, a search bar, or a comment section, user input is integral to the functionality of your application. However, it can also become an entry point for malicious activities if left unchecked.
Why Validate User Input:
- Mitigating Injection Attacks: Attackers can exploit unvalidated user input to inject malicious code into your application. This includes infamous threats like SQL injection and cross-site scripting (XSS). Proper validation drastically reduces the risk of such attacks.
- Data Integrity: Validating user input ensures that the data flowing into your application is consistent and matches the expected format. This helps maintain data integrity and prevents errors caused by unexpected information.
- Enhancing User Experience: You can guide users to input data in the correct format by providing real-time validation feedback. This not only prevents submission errors but also enhances the overall user experience.
Implementing Effective Input Validation in Laravel:
- Utilize Laravel’s Validation Rules: Laravel offers a robust validation system that includes a wide array of predefined rules. These rules cover everything from required fields and email formats to custom validation logic.
- Sanitize and Filter Input: Consider sanitizing and filtering user input alongside validation. Sanitization removes potentially harmful characters, while filtering ensures that information adheres to specific formats.
- Client-Side Validation: While server-side validation is paramount, supplement it with client-side validation using JavaScript. This provides instant feedback to users and reduces unnecessary server requests.
Best Practices for User Input Validation:
- Never Trust User Input: Treat all incoming user input as potentially malicious until proven otherwise. Validate and sanitize input even if it seems harmless.
- Whitelist Validation: Define an allowlist of allowed characters and formats for each input field. Reject input that doesn’t conform to these predefined patterns.
- Regular Updates: Like any other security practice, stay updated with Laravel’s latest validation features and best practices. This ensures you’re using the most effective tools available.
In the intricate realm of Laravel development, user input validation isn’t just a technical practice; it’s a shield that guards your application against many threats. By diligently validating user input, you’re bolstering your application’s security and reinforcing trust with your users. In the dynamic world of web development, where innovation meets vulnerability, validation is your steadfast ally in pursuing a secure and seamless user experience.
4. Protect Against SQL Injection

Shielding your digital fortress through meticulous Laravel development services involves a critical step: Protect against SQL injection. This threat arises when user inputs lack proper sanitation, potentially enabling malicious actors to manipulate SQL queries and gain unauthorized database access.
SQL injection attacks can lead to data exposure, alteration, or deletion. Laravel’s defences are robust. Its query binding technique parameterizes user inputs, preventing malicious SQL execution. The Eloquent ORM further enhances security by abstracting SQL interactions and automatically escaping values.
Adhering to best practices is paramount. Prioritize parameterized queries over direct concatenation, sanitize inputs, and conduct regular code audits to ensure secure methods. By fortifying your Laravel application against SQL injection, you’re erecting a robust barrier against a damaging vulnerability while providing your Laravel development services maintain the utmost integrity and user trust.
5. Cross-Site Scripting (XSS) Prevention
In securing your digital haven with proficient Laravel development practices, countering Cross-Site Scripting (XSS) emerges as a pivotal measure. XSS occurs when malicious code infiltrates a website through unfiltered user inputs, potentially compromising user data and integrity.
The gravity of XSS lies in its ability to expose sensitive information or perform malicious actions under the user’s identity. Laravel offers potent tools to thwart such threats:
- Blade Templating: Laravel’s Blade templating engine automatically escapes variables, preventing unintended script execution.
- XSS Middleware: Laravel provides built-in middleware for encoding user inputs, adding an extra layer of protection.
- Content Security Policy (CSP): Implementing CSP headers in your Laravel application restricts the sources from which content can be loaded, reducing the risk of XSS attacks.
Adhering to these precautions is essential. Validate and sanitize inputs, embrace Laravel’s security features, and implement a robust CSP. By guarding against XSS vulnerabilities, you ensure your Laravel development maintains a resilient and trustworthy digital presence.
6. Implement HTTPS and SSL
In web application development, particularly in Laravel, bolstering security is paramount. A crucial step in this pursuit is the implementation of HTTPS and SSL protocols. These measures are essential to safeguard sensitive data transmitted between users and your application.
HTTPS (Hypertext Transfer Protocol Secure) encrypts the data between users’ browsers and your application’s server, thwarting potential eavesdropping and tampering. SSL (Secure Sockets Layer) certificates are the foundation of this encryption, ensuring that communication remains confidential.
Advantages of HTTPS and SSL:
- Data Encryption: HTTPS encrypts data during transit, preventing unauthorized access to sensitive information.
- Trust and SEO: SSL certificates enhance user trust, as indicated by the padlock symbol in browsers. Search engines also favor HTTPS websites, improving SEO rankings.
- Authentication: SSL certificates verify your application’s authenticity, shielding users from potential phishing sites.
Implementing HTTPS and SSL involves obtaining a valid SSL certificate and configuring your Laravel application for secure connections. By adopting these measures, you’re securing your web application development, fostering trust among users, and ensuring compliance with modern security standards.
7. Secure Session Management
In web application development, security isn’t just a feature—it’s a necessity. A crucial aspect of building a robust and trustworthy application is ensuring secure session management. Sessions are pivotal in maintaining user interactions and data, making their protection paramount.
Laravel offers robust mechanisms to fortify session management:
- Session Encryption: Laravel automatically encrypts session data, preventing unauthorized access and ensuring confidentiality.
- CSRF Protection: Cross-Site Request Forgery (CSRF) attacks can compromise sessions. Laravel’s built-in CSRF protection safeguards against such threats.
- Expire and Regenerate: Set session expiration times and periodically regenerate session IDs to minimize the window of vulnerability.
By implementing secure session management practices in your web application development, you create a shield against unauthorized access and data breaches. This preserves user trust and solidifies your commitment to crafting applications that prioritize security and integrity.
8. Protect Against Cross-Site Request Forgery (CSRF)
Safeguarding web applications is a top priority in Laravel development. To fortify your digital haven, countering Cross-Site Request Forgery (CSRF) threats is crucial. CSRF attacks manipulate authenticated users into executing malicious actions unknowingly. Laravel provides a robust defense:
- CSRF Tokens: Laravel automatically generates unique tokens for each user session, validating the authenticity of requests.
- Middleware Protection: Laravel’s built-in CSRF middleware verifies tokens, preventing unauthorized requests from being executed.
By integrating these measures, you fortify your Laravel application against CSRF vulnerabilities. This secures user interactions and demonstrates your commitment to proactive security practices in modern web development.
9. Harden Configuration and File Permissions
In the landscape of Laravel security, enhancing configuration settings and file permissions is a critical stride. Securing sensitive files, such as configuration files, shields against unauthorized access and potential breaches. Laravel’s framework offers key tactics:
- Restricted Access: Limit access to sensitive configuration files by setting appropriate permissions. This prevents unauthorized users from tampering with vital settings.
- Environment Configuration: Store sensitive data in environment files and never expose them in version control. Laravel’s .env file shields sensitive variables from prying eyes.
By meticulously configuring permissions and safeguarding critical files, you erect a solid barrier against potential threats. This reflects an unwavering commitment to fortifying your Laravel application and upholding security standards in modern web development.
10. Use Content Security Policy (CSP)
Bolstering security in Laravel involves advanced tactics, including a Content Security Policy (CSP). CSP guards against cross-site scripting (XSS) and data injection attacks. It achieves this by specifying approved content sources, mitigating the risk of malicious script execution. Laravel’s integration of CSP fortifies your defense:
- Malicious Content Mitigation: CSP curtails the potential impact of XSS attacks by regulating the domains from which content can be loaded.
- Policy Customization: Laravel empowers you to tailor CSP rules to suit your application’s specific requirements, balancing security and functionality.
By embracing CSP, you establish a robust security framework that exemplifies Laravel’s commitment to secure, modern web development practices.
Related Article: 11 Successful Websites Developed Using Laravel
Top Laravel Security Packages for Developers
In the realm of Laravel development, ensuring robust security is paramount. Several key packages aid developers in fortifying their applications. Here are three notable options:
- Laravel-ACL: Access Control Lists (ACL) are fundamental to controlling user permissions. This package simplifies ACL implementation, offering granular control over user access to different parts of your application.
- Laravel Security: As the name suggests, this package enhances overall security. It provides features like XSS protection, safe redirects, and content filtering, contributing to a fortified application.
- Laravel Security Component: This package takes security up a notch by integrating robust security components. It includes encryption, hashing, validation, and more tools, streamlining your security efforts.
For a Laravel development agency, these packages are invaluable assets. By incorporating them into your development process, you expedite security implementation and establish a strong foundation for crafting secure, reliable applications that clients can trust.
Conclusion
In the intricate realm of Laravel security, these checkpoints act as sentinels, fortifying your application’s defenses. Secure authentication, vigilant updates, meticulous validation, and shielded configurations create a robust bastion. Protection against threats like SQL injection, XSS, and CSRF forms an unbreachable wall. Implementation of HTTPS, secure session handling, and CSP reinforce your fortifications. Familiarity with essential security packages like Laravel-ACL, Laravel Security, and Security Component adds the final layer. As a Laravel developer, embracing these measures ensures your applications are secured, and your expertise is unwavering in the face of evolving threats.